Our service
At TZAMON Information Technology, we offer tailored tech solutions, cutting-edge technology, expert guidance, seamless integration, and ongoing support. Our goal is to simplify your tech experience and help you thrive in the digital world.

Customized Solutions: We tailor our services to fit your specific needs. Whether you need software development, network setup, cybersecurity solutions, or cloud migration, we’ve got you covered with personalized solutions
We bring you the latest and greatest in tech. From software applications to hardware solutions, we offer cutting-edge products to boost your productivity and keep you ahead of the curve
Our team of experts is here to guide you through the tech jungle. Whether you’re planning an upgrade, implementing new technology, or securing your data, we provide expert advice to help you make the right decisions
Getting started with our services is a breeze. We seamlessly integrate our solutions into your existing systems, ensuring minimal disruption and maximum efficiency.
We’re here for you every step of the way. Our support team provides ongoing assistance to keep your systems running smoothly, troubleshoot any issues, and ensure you get the most out of our services
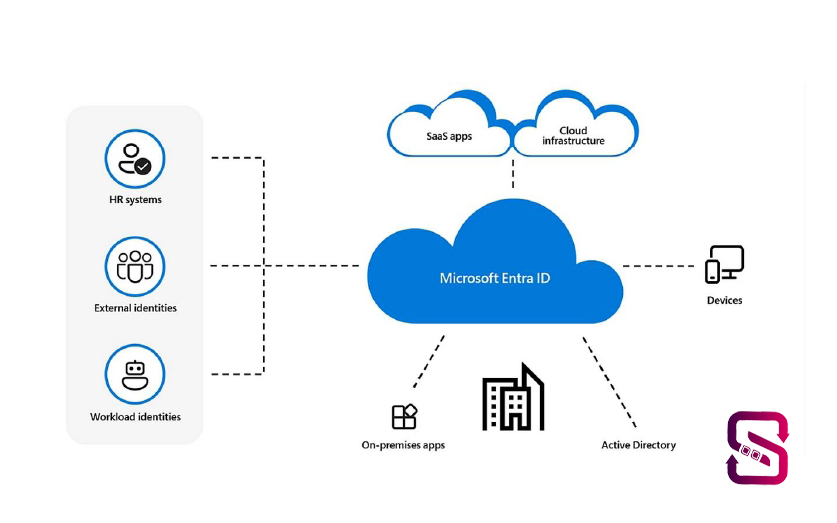
Azure ARC
Azure Arc extends Azure’s management capabilities to resources outside of Azure, including on-premises servers, Kubernetes clusters, and resources in other clouds. This means you can use Azure management tools and services to manage, govern, and secure these resources wherever they are, providing a consistent and unified experience across your entire hybrid and multi-cloud environment. In essence, Azure Arc enables you to bring Azure services to any infrastructure, allowing you to leverage the power of Azure management wherever your resources reside


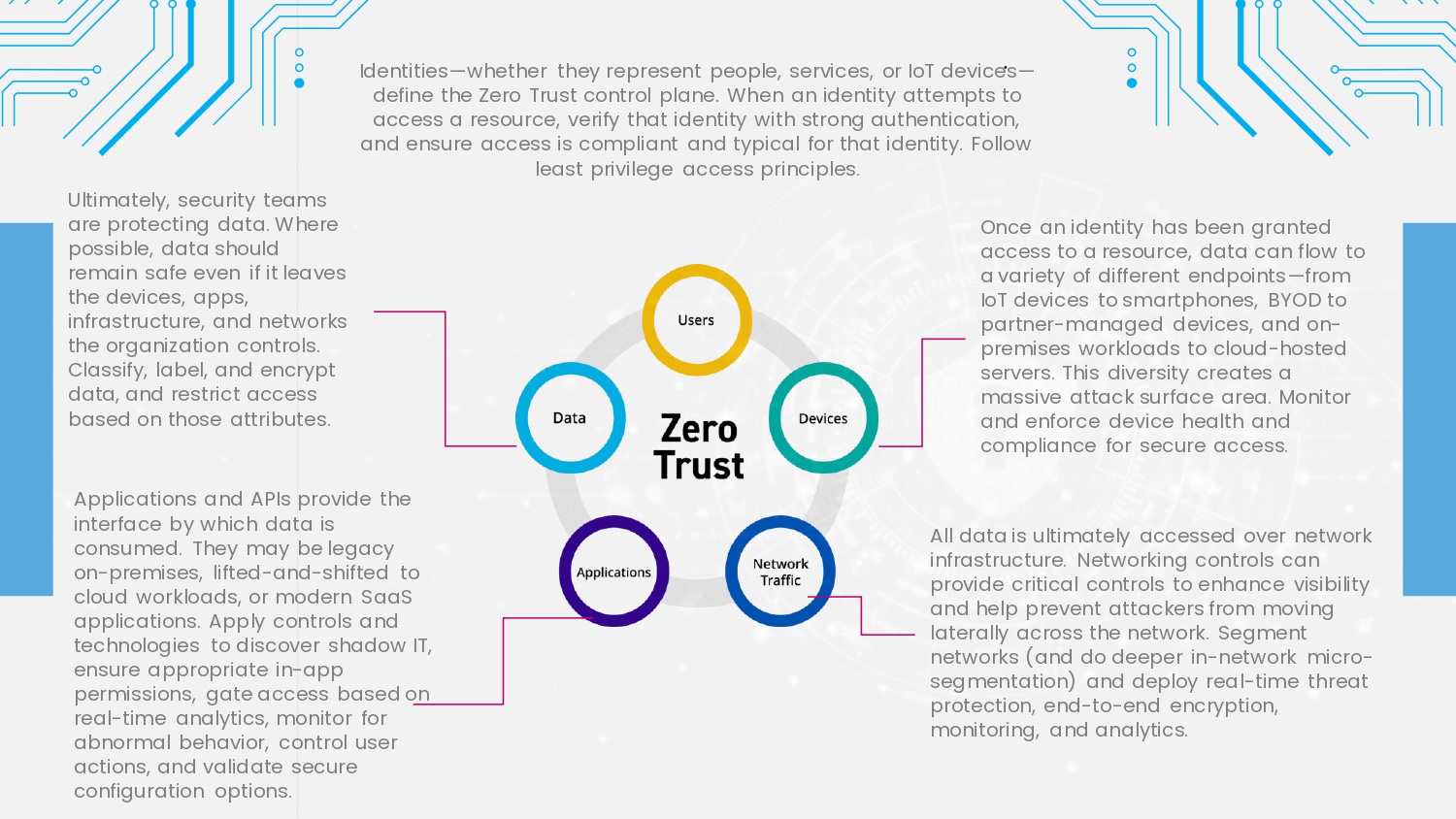
Microsoft Entra ID Protection
Microsoft Entra ID Protection helps
organizations detect, investigate, and
remediate identity-based risks. These
identity-based risks can be further fed
into tools like Conditional Access to
make access decisions or fed back to a
security information and event
management (SIEM) tool for further
investigation and correlation.